Say goodbye to outdated VPN solutions
Global Secure Access
Remote work has fundamentally transformed the workplace, prompting companies to reconsider how to ensure secure access to data and applications. The answer lies in Security Service Edge (SSE).

Security for a connected work environment
Microsoft introduces Global Secure Access, a central Security Service Edge (SSE) solution for security management that operates both in the cloud and on-premises. Comprehensive security is achieved through the integration of Zero Trust principles, which emphasize robust identity protection and conditional access. This allows for the granular establishment of different rule sets for specific services, whether they are cloud-based or on-premises. Discover the details of how Microsoft's Security Service Edge (SSE) functions in our webcast on the topic.
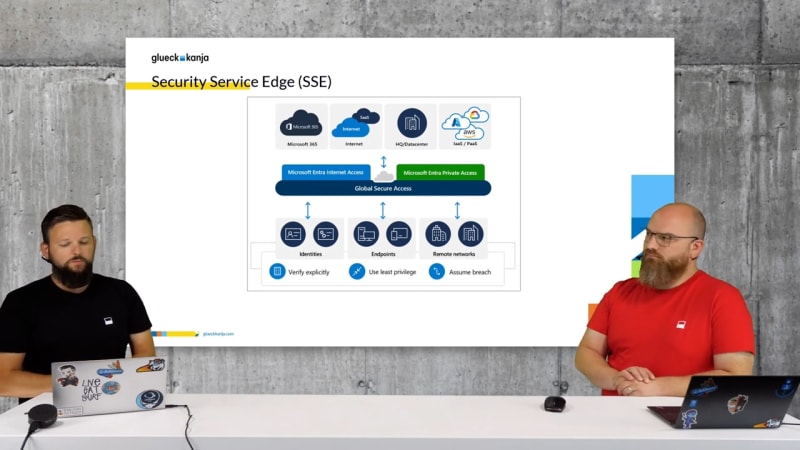
Microsoft's Security Service Edge (SSE)
Global Secure Access is designed to deliver security services through the cloud, supporting managed devices across all major platforms. This includes integration with identity providers and security tools such as XDR or SIEM.The architecture of the SSE solution is divided into two main areas, each with different components:
- Internet Access features an identity-centered Secure Web Gateway (SWG) that functions similarly to a forward proxy. It not only protects against malware and other threats but also performs URL category filtering.
- Private Access is an identity-centered Zero Trust Network Access (ZTNA) solution that allows granular and consistent access to non-public applications regardless of their location, implementing detailed context-based access control.
Integration
Entra Governance
- Integration with Identity & Access Management and Identity Governance features of Entra
- App segments are mapped as enterprise apps
- Uses features such as dynamic groups and access packages
Conditional Access
- Integration in Conditional Access right from the start
- Securing defined resources with Conditional Access
- Use of the solution as an access condition for resources
XDR & SIEM
- Integration with Microsoft's own security products
- Use of the logs generated by Global Secure Access in Sentinel
- Direct influence of the device risk from Defender for Endpoint on Conditional Access
- Announced integration with Defender for Cloud Apps as a CASB component in XDR
Use Cases

Enhance the protection of your corporate data with the "Tenant Restrictions" feature of Global Secure Access. This function extends the existing "Guest Restrictions" and allows you to precisely control from which tenants users are allowed to log in. This control is crucial for compliance and effectively protects your corporate resources from unauthorized access.
Private Access seamlessly replaces existing VPN infrastructures and significantly increases security standards through integration into Conditional Access. The "Quick Access" configuration used enables a gradual segmentation of network access, supported by advanced integrated reporting. Each of these segments can then be comprehensively secured through detailed control mechanisms.
Many companies face challenges due to IP and location discrepancies when using SWG solutions in combination with Microsoft 365 services. The general recommendation is therefore to exclude access via third-party proxies and SWGs. Microsoft has recognized this issue and responded with the introduction of IP Address Restoration. This solution can also be effectively used in coexistence scenarios, as Microsoft has privileged access to the Windows network stack.
Outlook
With the continuous advancement of Global Secure Access technologies, Microsoft is adapting to the increasingly complex demands of network security. These innovations not only ensure the security of your data but also enable specific customization of access to corporate applications, paving the way for a more detailed and effective security infrastructure. Stay tuned for the next steps in the evolution of network security!