Global Secure Access Unlocked
This blog explores how Microsoft Global Secure Access enhances security and control in our Managed Red Tenant. With Entra Internet Access and Private Access, organizations can secure admin sessions, enforce Zero Trust, and streamline access to cloud and on-prem resources. Real-world use cases and architecture insights show how to protect M365 environments effectively.

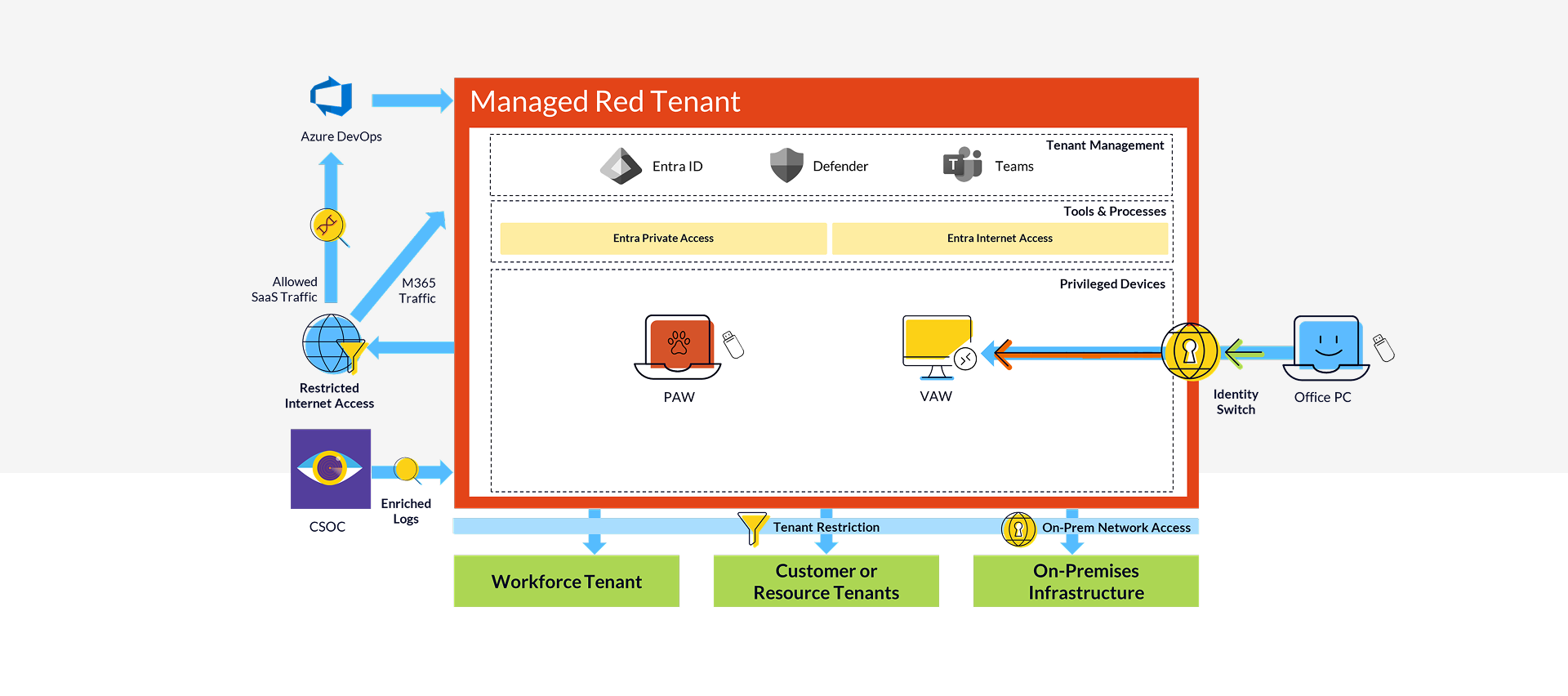
What is a Managed Red Tenant?
The Managed Red Tenant combines our extensive experience in managed services with proven blueprints in the areas of workplace, Azure, and security.
The result: An isolated, fully cloud-based as-code managed environment that effectively protects administrative users and endpoints – even in target environments with multiple Microsoft Entra tenants and Active Directory domains.
Our solution relies on native, cloud-based identity and security features from Microsoft and strictly adheres to Zero Trust principles.
Global Secure Access as Security Service Edge
We have integrated the latest innovations from Global Secure Access into various components of the Managed Red Tenant to enhance security when accessing Virtual Access Workstations (VAWs) and to protect and restrict outgoing privileged access.
Microsoft Entra Internet Access
functioning as an identity-centric Secure Web Gateway (SWG), has been implemented to block public internet access and restrict connectivity to privileged interfaces and the authorized company’s tenant environments only. Additional features, such as Universal Conditional Access Evaluation (CAE), enable near real-time access blocking.
Microsoft Entra Private Access
serves as an identity-centric Zero Trust Network Access (ZTNA) solution and is the core of our approach to providing secure and private access to VAWs. Its integration into our solution adds an extra layer of protection for privileged sessions on AVD-based endpoints by enforcing Conditional Access on the accessing client before establishing connectivity to the VAW. Securing access and applying Zero Trust principle to manage private or on-premises resources is another use cases where we take benefit of Private Access.
Use Cases for Global Secure Access in the Managed Red Tenant
Global Secure Access is one of the core components in the design of our Managed Red Tenant, and we’re excited to elevate both security and usability to a new level. The added value becomes most evident when looking at the individual use cases, which we’ll showcase in this blog.
Access to Virtual Access Workstations
Some organizations choose not to equip all administrators with physical Privileged Admin Workstations (PAWs). For these low-privileged admins, we offer what we call Virtual Access Workstations (VAWs).
The most critical aspect here is secure access to the VAWs, and we consider it essential to establish a high level of security—where Entra Private Access plays a key role.
Administrators connect to the VAWs from their enterprise devices and sign in using their account from the Managed Red Tenant. Because of this identity switch, the accessing user is sourced from a different tenant than the the original device and will not able to present a device compliance status.
Therefore, we are using global secure access for pre-authentication using the original user from the device. Since our VAWs do not expose public endpoints and are only accessible via Entra Private Access, we can secure network access to a very high degree. Conditional Access in the workforce environment enforces strong user and device authentication, including device compliance and risk-based controls.
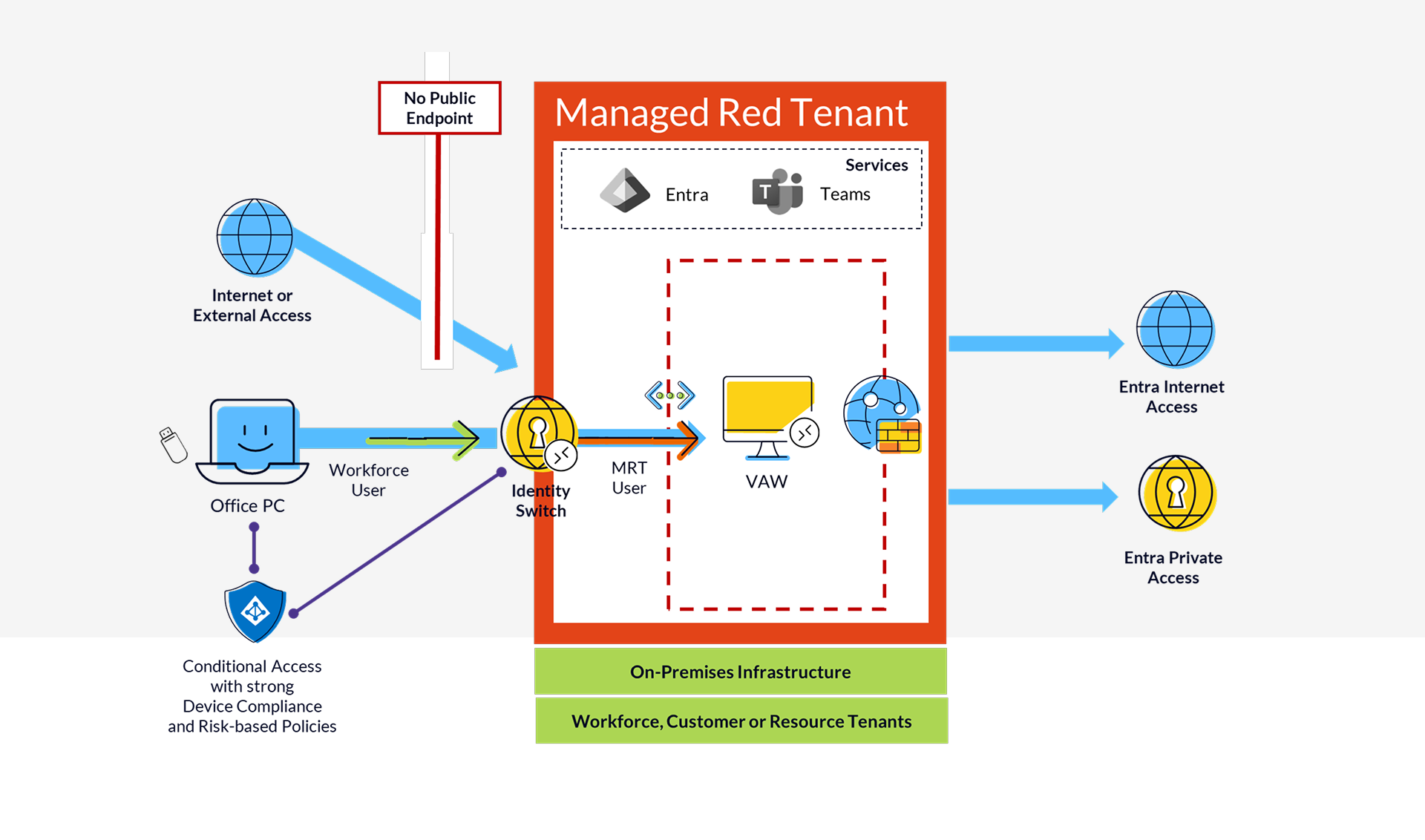
Secure Web Filtering
A key characteristic of administrative devices is their strictly limited access to applications, designed to minimize the attack surface as much as possible. While local solutions such as proxy.pac files or shared centralized proxies (not T0 exclusive) were commonly used in the past, we’ve opted for Entra Internet Access for devices within the Managed Red Tenant.
- Internet access is only permitted from compliant devices and after strong user authentication
- Access is restricted to explicitly approved URLs, and since HTTPS traffic (where possible) is decrypted and inspected, it’s also feasible to limit access to specific paths—for example, within Azure DevOps or GitHub
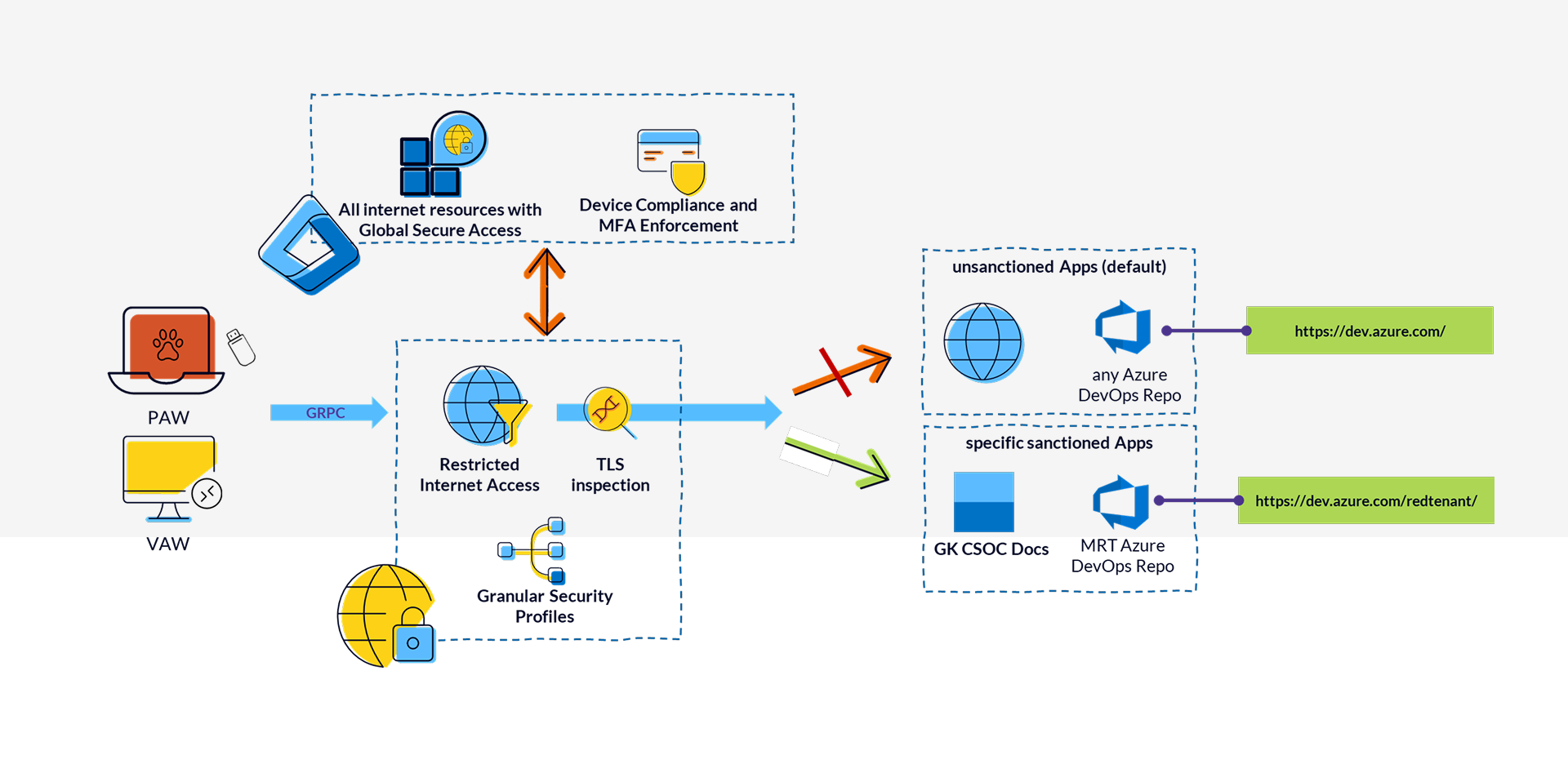
Tenant Restrictions for SaaS Services and Administrative Interfaces
In SaaS services and administrative interfaces, it’s common for URLs to be identical across all tenants, which makes them difficult to control using the web filtering methods described above.
To ensure that only accounts from the Managed Red Tenant can sign in to Microsoft’s approved portals from an administrative device, we leverage the Tenant Restriction feature of Global Secure Access.
Through Entra Internet Access, Entra ID is signaled which tenants are permitted for sign-in. This guarantees that all policies from the Managed Red Tenant are enforced and that administrative access occurs exclusively via B2B collaboration.
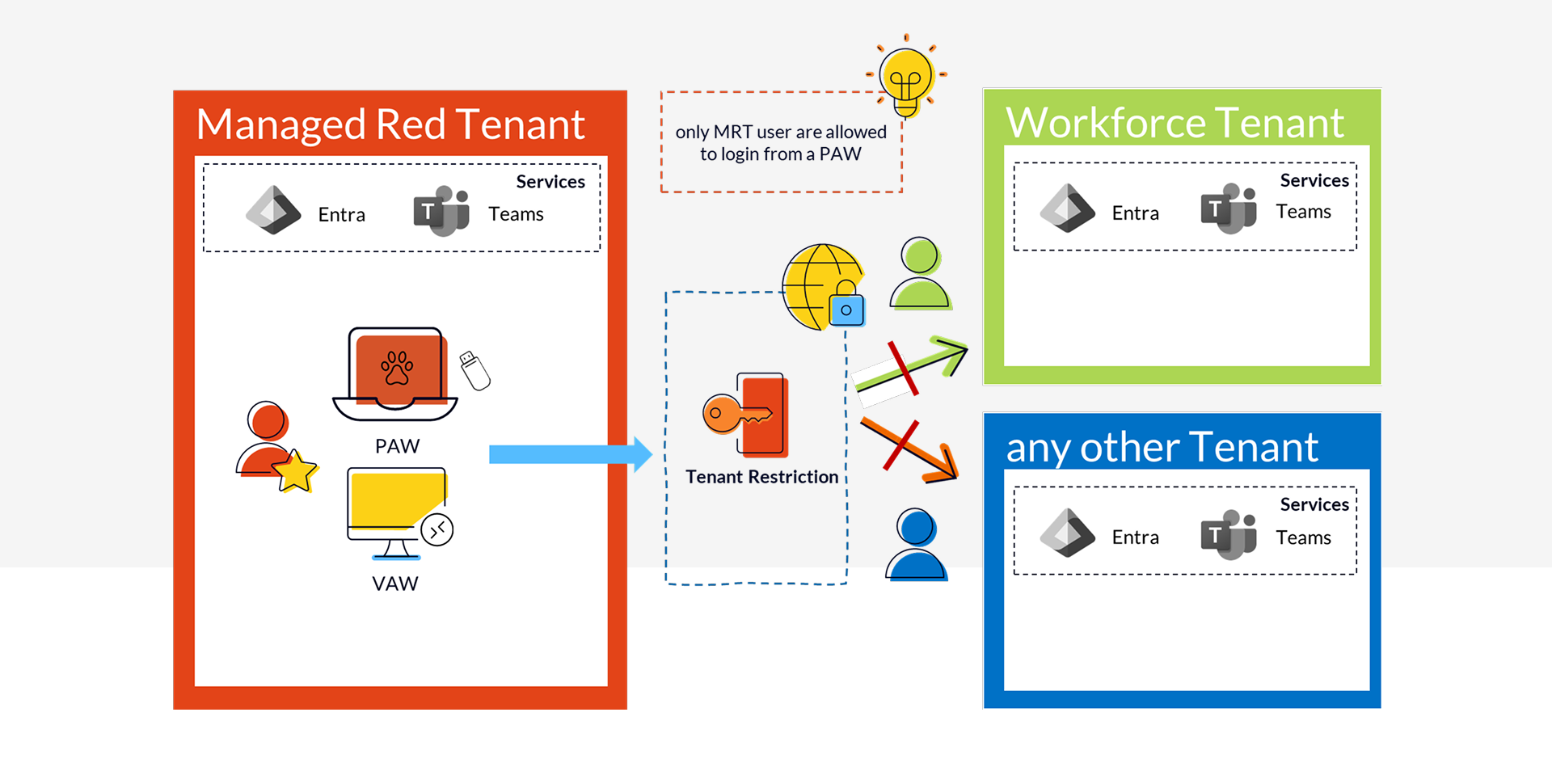
On-Premises Access
Of course, a Managed Red Tenant can also be used to administer on-premises and IaaS environments, which requires secure access to the datacenters. Entra Private Access provides us with Zero Trust Network Access that combines top-tier security standards with a flexible architecture and strong performance.
Access to datacenters and IaaS environments depends on robust user and device authentication, including device compliance and risk-based controls.
Managing individual targets as app segments enables granular access control, which is automated using Entra Governance features. This extends functions already widely used in the Managed Red Tenant—such as Just-In-Time administration and approval workflows—into the network layer.
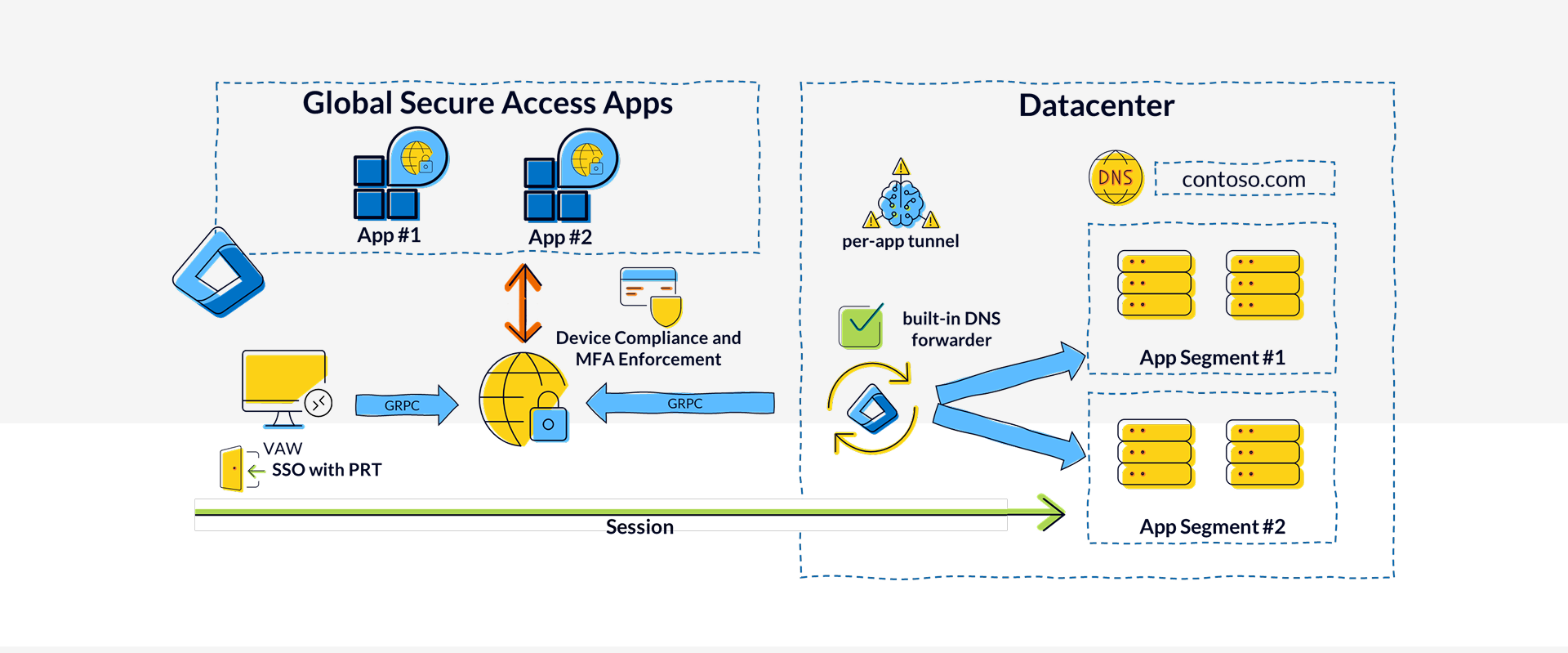
Revocation Access in Near Real-Time
Zero Trust also means being prepared to quickly and effectively contain threats—even within the most secure architecture—and to isolate compromised components.
In a Managed Red Tenant environment, we’re not only prepared for the compromise of users and devices within the tenant itself, but also for the (most likely) scenario where an attack originates from an admin’s office PC and then propagates to the Virtual Admin Workstation.
Thanks to the Universal Continuous Access Evaluation (CAE) feature in Global Secure Access, the following actions are automatically triggered:
- Access to the Virtual Admin Workstation via Entra Private Access is interrupted if, for example, the user risk level of the account in the Workforce Tenant is set to High
- Access to admin interfaces and the datacenter environment is revoked if, for example, the sessions of the account in the Managed Red Tenant are terminated
Additionally, full isolation of all devices and accounts within the Managed Red Tenant can be initiated at any time by the integrated CSOC service.
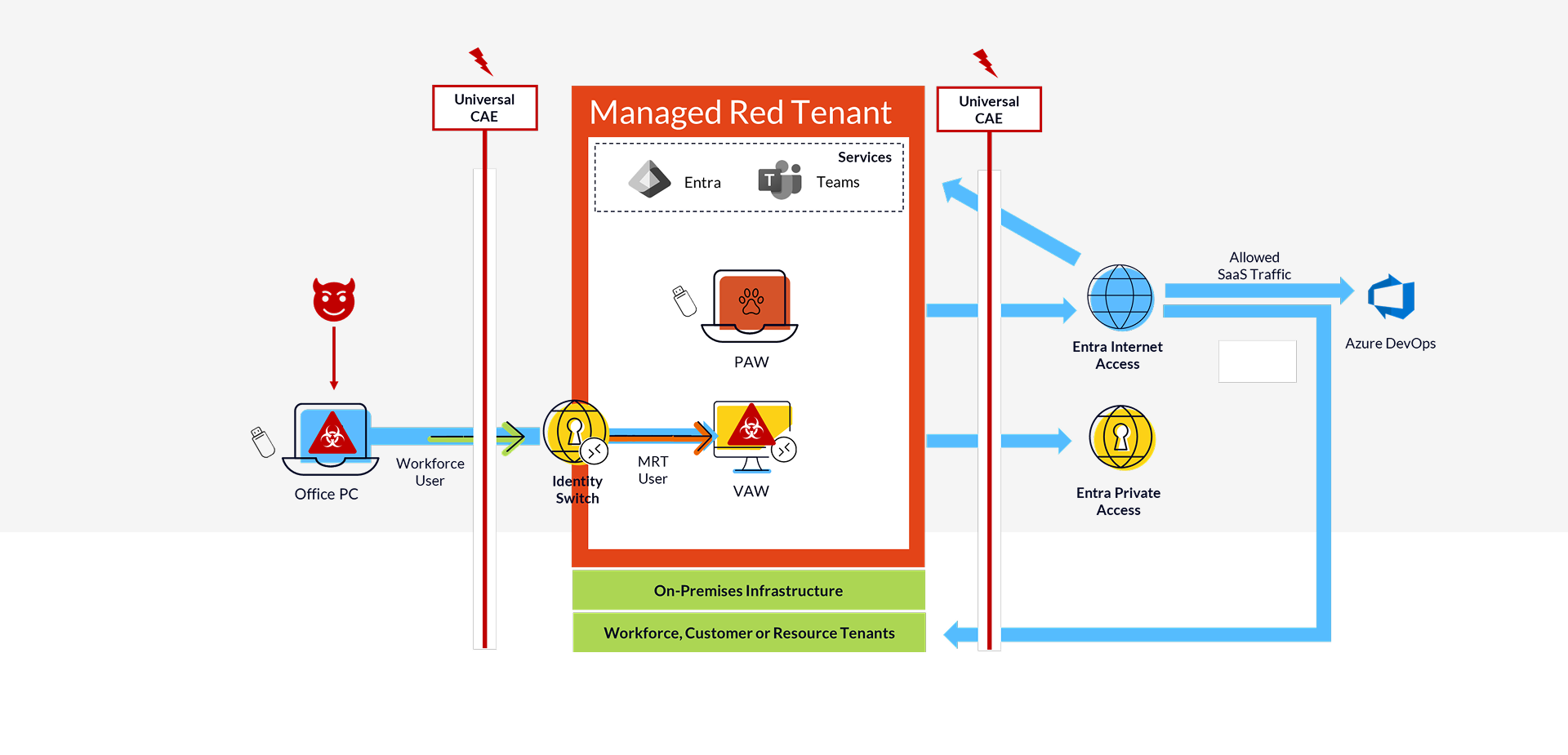
Enriched Sign-Ins and Token Insights
Beyond its many features for access control, Global Secure Access is a true game changer when it comes to logging. We gain significantly more telemetry from the network layer and can correlate it with existing sign-in and audit logs.
This enables our CSOC to identify which actions were still performed after containment was triggered—for example, in cases where not all tokens supported Continuous Access Evaluation (CAE).

Final thoughts
This blog is published alongside a webcast where we explore the Managed Red Tenant, Global Secure Access, the integration process, and the relevant use cases, supported by live demos.
If this blog has sparked your interest, we definitely encourage you to check out the webcast. And of course, we’re always happy to hear from you directly!
Global Secure Access Unlocked: Real World Implementation in Managed Red Tenant
In the Managed Red Tenant, we enforce strict separation for privileged access. Live demos will show how we secure admin workflows using Global Secure Access.
In our English-language session, you’ll learn:
- How PAWs and VAWs with identity switching create secure admin workstations
- How Tenant Restrictions and Cross-Tenant Access Policies allow only authorized access
- How Per-App Tunnels and Continuous Access Evaluation are replacing traditional VPNs
- How Just-in-Time administration works in practice with Microsoft PIM