Practical technical implementation of the NIS2 Directive
The NIS2 Directive requires many organizations to put baseline cybersecurity measures in place. Our proven, practical solutions help you meet those requirements efficiently — standardized, secure and scalable.
10 Microsoft MVPs, four with a security focus
BSI-certified APT response provider
ISO 27001-certified service
Extensive expertise in Workplace, Security and Azure
What is NIS2 and what does it mean for your organization?
Since October 2024 the new EU NIS2 Directive has been in force, setting binding cybersecurity standards across Europe. Its aim is to create a uniform level of security throughout the European Union and to better protect organizations from digital threats. It applies to companies providing critical or essential services, and their supply chains are also covered by the new requirements. Organizations within the scope are required to implement concrete security measures. Acting now reduces risks, protects your company — and helps avoid fines and personal liability for management.
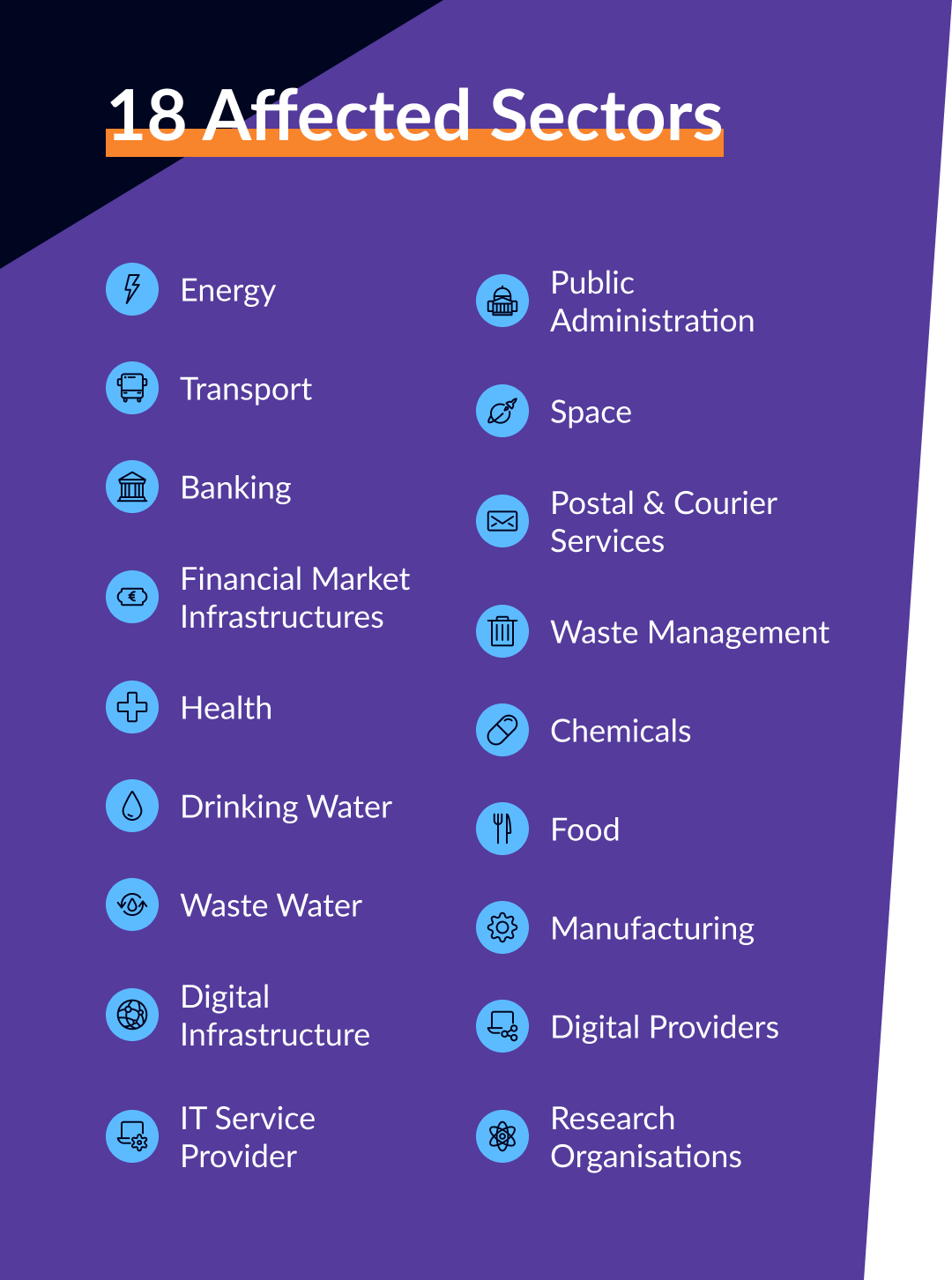
Sectors affected by the NIS2 Directive
What specific measures does NIS2 require?
Reduce risks through targeted security measures
| Risk Measures | GK Services | NIS2 | CSOC | APT Response | Preventive Services | Managed Red Tennant | AzERE | Data Security | Workplace/ Azure |
|---|---|---|---|---|---|---|---|---|
| Risk Analysis and Information System Security | 12.2 a) | |||||||
| Incident Handling | 12.2 b) | |||||||
| Business Continuity | 12.2 c) | |||||||
| Supply Chain Security | 12.2 d) | |||||||
| Security in Network and Information Systems | 12.2 e) | |||||||
| Effectiveness of Cybersecurity Risk Management Measures | 12.2 f) | |||||||
| Basic Computer Hygiene Practices and Cybersecurity Training | 12.2 g) | |||||||
| Cryptography | 12.2 h) | |||||||
| Human Resources Security, Access Control Policies and Asset Management | 12.2 i) | |||||||
| Multifactor Authentication or Secured Communication | 12.2 j) |
Achieving NIS2 Compliance in 3 Steps
- Applicability AssessmentApplicability AssessmentA specialized service provider or law firm assesses whether – and to what extent – NIS2 applies to your organization. This gives you a solid evaluation of your exposure and a clear basis for understanding which requirements need to be considered as you move forward.
- Gap AnalysisGap AnalysisThe analysis highlights which measures are already in place and where action is required. Based on proven frameworks, we derive pragmatic technical and organizational steps—from kick-off through audit and evaluation to the final set of recommendations.
- Action PackageAction PackageWhile our Managed Services based on Microsoft technologies support you in defining and implementing the technical measures, a partner helps you close the remaining organizational gaps.











