Vulnerablity Management with Microsoft 365 Defender
In order to prevent attacks effectively, early detection of security vulnerabilities and their elimination, for example by applying patches, is essential. Given the increasingly narrow time span between the discovery of a security vulnerability and the first attacks targeting it, efficient and well-structured vulnerability management is becoming increasingly important.

We all want to avoid security incidents in IT and therefore need to know our attack surface and reduce it wherever possible. In addition to tools such as Microsoft Defender Vulnerability Management, smooth processes in application management and vulnerability management are particularly helpful.
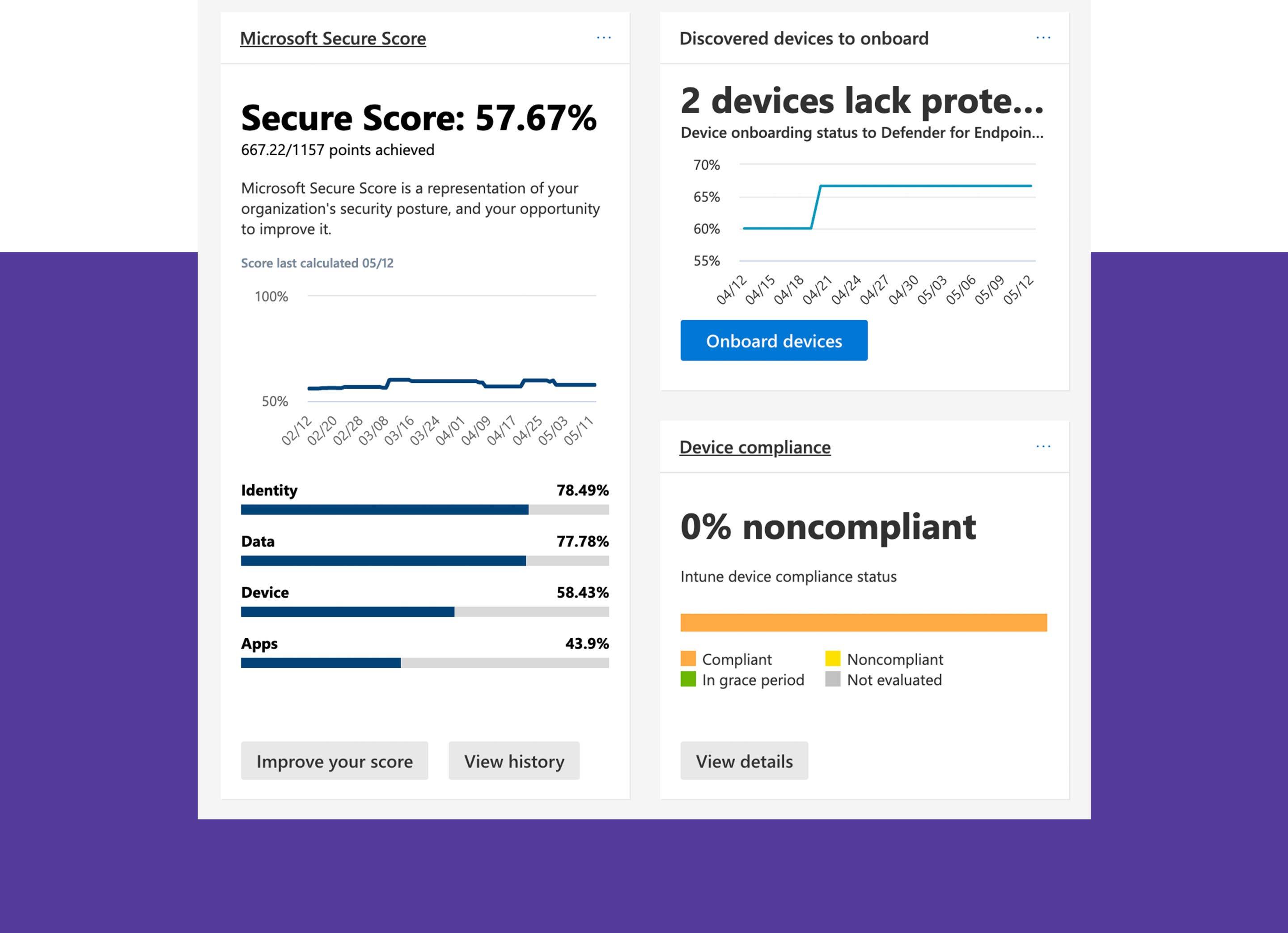
Looking at the Microsoft 365 Defender Portal, especially Defender for Endpoint, many are amazed at the data collected on vulnerable applications and weak configurations. Who hasn’t experienced it? Every month, new update recommendations for Windows 10, Office and Google Chrome pop up in the dashboard. There are around 70 recommendations for secure endpoint configurations on the list as well. The question is how to cope with the countless recommendations and achieve an acceptable Exposure or Secure Score. What would be an acceptable score for an enterprise and how should one measure? To answer these questions, let’s first take a look at the various products and scores.
Features in Microsoft 365 Defender Portal
The Microsoft 365 Defender Portal contains the overall Secure Score, which covers all areas of the M365 tenant, including endpoints, identities, data, and applications. A high score signals maximum security configurations. Microsoft recommends the most secure configuration of each tool and compares it to the current tenant configuration. Each individual Defender product has its own score (for example, Secure Score for Devices or Identity Secure Score), which is included in the general Secure Score. This score increases as soon as the settings recommended by Microsoft have been correctly implemented or mitigated by alternatives.
With Defender for Endpoint, we get a detailed listing of vulnerabilities on endpoints such as Workplace, Servers and Mobile Devices. This includes vulnerable applications, but also insecure configurations, such as a disabled Attack Surface Reduction Rule. In the future, the Defender for Vulnerability Management add-on will provide even more insights into browser extensions, certificates and firmware data. In addition, vulnerable applications can be blocked in the future.
Meaning of the Secure Score for Devices and the Exposure Score
There are two scores in the Threat & Vulnerability Management (TVM) module of Defender for Endpoint: The Secure Score for Devices is part of the general Secure Score and only evaluates endpoints. The Exposure Score, on the other hand, indicates how vulnerable the devices are. The higher the Exposure Score, the more vulnerabilities there are on the devices. Therefore, the goal is to keep the Exposure Score as low as possible. If Microsoft’s recommendations are followed, the Exposure Score decreases and the Secure Score usually increases. The recommendations differ between configuration changes and software updates. It often takes a team of security, workplace, network and server managers to work through the recommendations regarding configurations.
Challenges and solutions for software updates and upgrades
Unfortunately, the recommendations for software updates or upgrades are not so easy to handle. Application vulnerabilities in particular are very volatile - why else would there be a patch day every month? So we will always have a high exposure score due to new software vulnerabilities. Acute measures are often not helpful here; functioning update processes must be implemented in the company.
Microsoft Defender External Attack Surface Management
In addition to your own endpoints and servers, there is another large attack surface. Externally accessible systems can be monitored with Microsoft Defender External Attack Surface Management. The unknown vulnerabilities are not a black box, we recommend regular assessments regarding the infrastructure, and a PenTest or Red Teaming events can also reveal unknown attack surfaces.
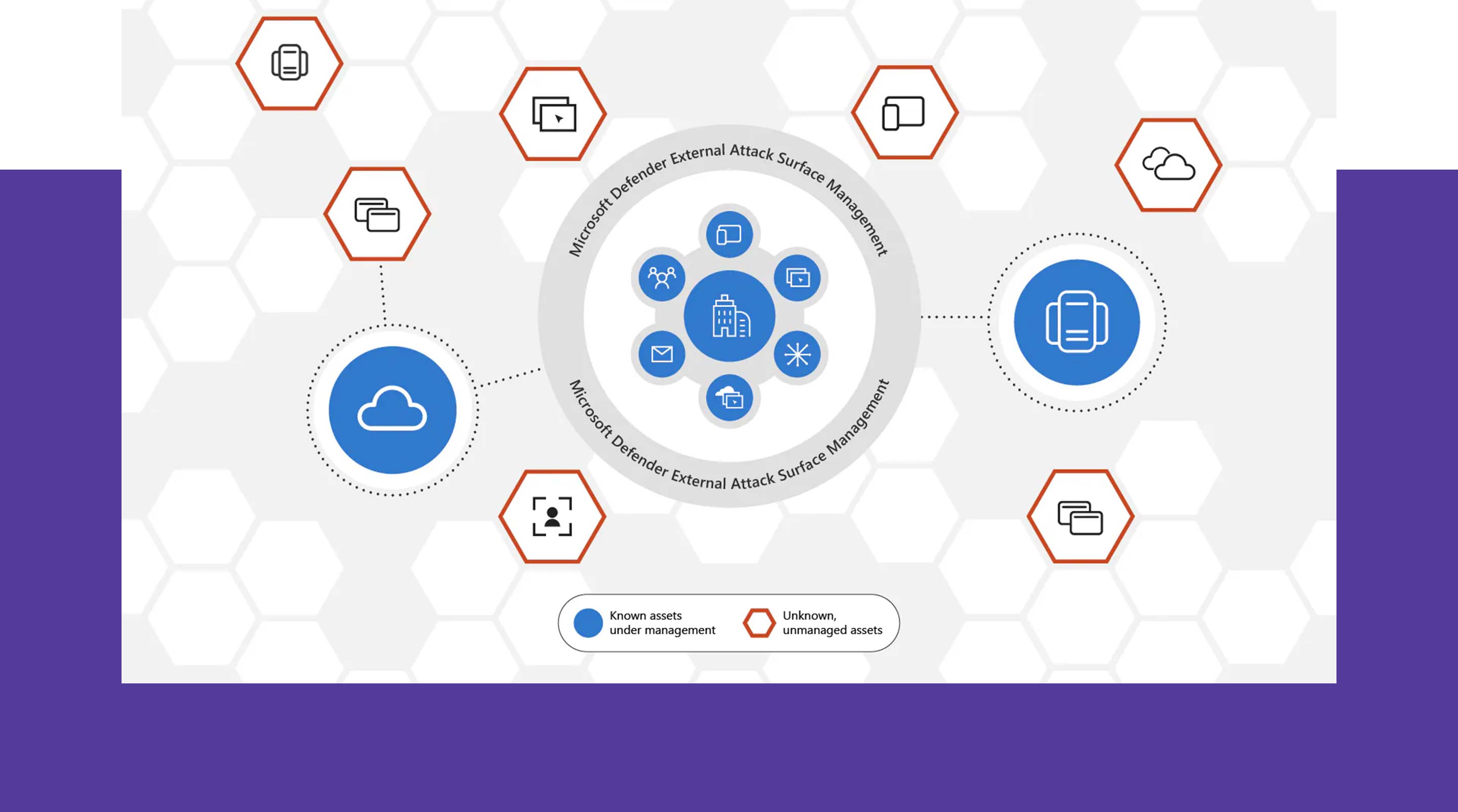
Microsoft currently offers the possibility of providing a comprehensive overview of its own attack surface and the existing vulnerabilities. However, mitigation or reducing the vulnerabilities requires a great deal of effort and usually new processes.