Zero-Day Exploit in Outlook enables theft of Net-NTLMv2 hash
Microsoft confirmed a critical vulnerability in Outlook that is already being used by attackers to steal the Net-NTLMv2 hash from users. Once activated by a malicious email, this exploit allows further attacks on the victim. Microsoft recommends updating the Office package to fix the vulnerability. Various update options are available for this purpose.

Microsoft has confirmed on Tuesday that a critical Outlook security vulnerability, rated 9.8 out of a maximum of 10 points, is already being exploited in the wild (Zero-Day). What’s dangerous about this exploit is that it executes as soon as a malicious email is delivered to Outlook. The email does not need to be opened to exploit the vulnerability, so no additional user activity is required. With a manipulated email, an attacker can specifically target a server under their control and thereby capture the Net-NTLMv2 hash of the logged-in user. The stolen information can then be used for further attacks against the user’s on-premises infrastructure.
The most important measure to address this exploit is to immediately update the Office package. The following update measures are possible:
- The user checks for updates in Office themselves: (File \ Office Account \ Update Options > Update Now)
- In a modern workplace environment, we use Office update policies. Office can be managed using Intune or GPOs. We recommend using the deployment deadline setting.
We will show you how to achieve basic settings for quickly updating Office applications using Intune. These instructions are not complete but focus on quickly installing updates.
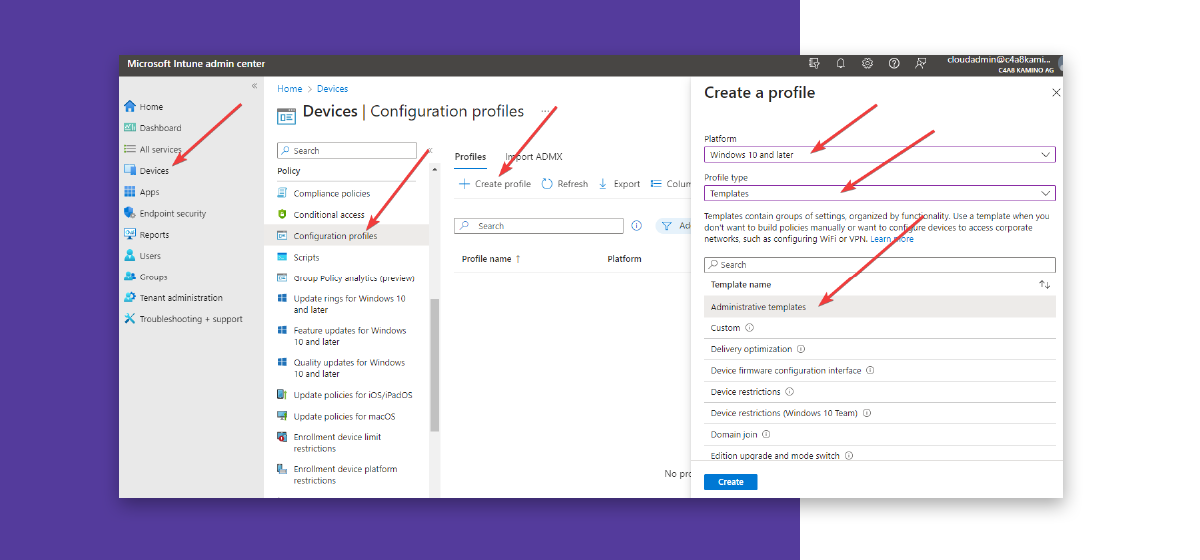
In the Intune portal, open the Devices section.
Click on “Configuration profiles” and then “Create profile”.
Choose “Windows 10 and later” as the platform and “Templates” as the type.
Then click on “Administrative Templates”.
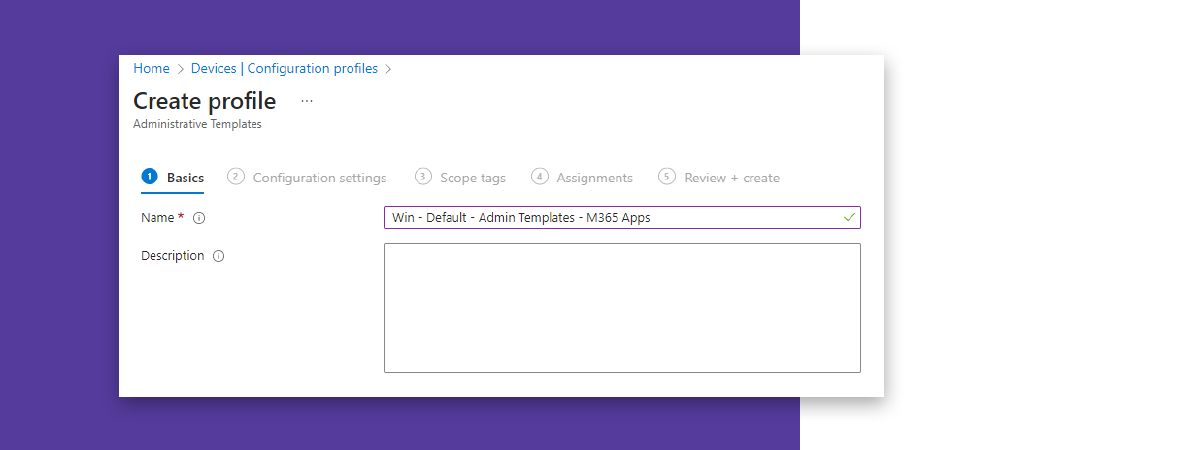
Assign an appropriate (any) name.
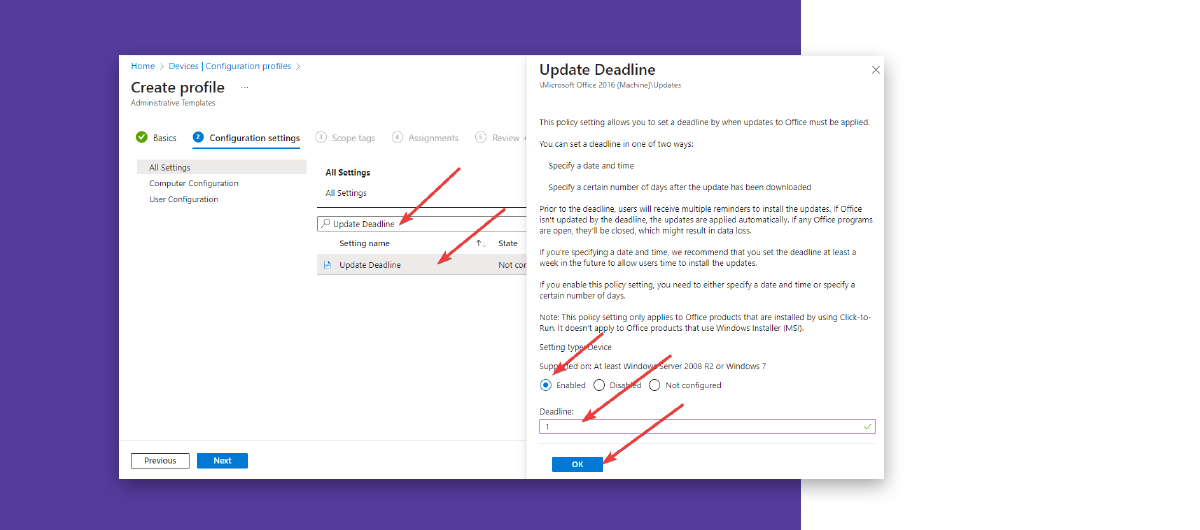
In the search bar, enter “Update Deadline” and then click on the entry.
Activate the setting and set a deadline. This can be a number of days or a specific time. Click “OK” (and not “Next”).
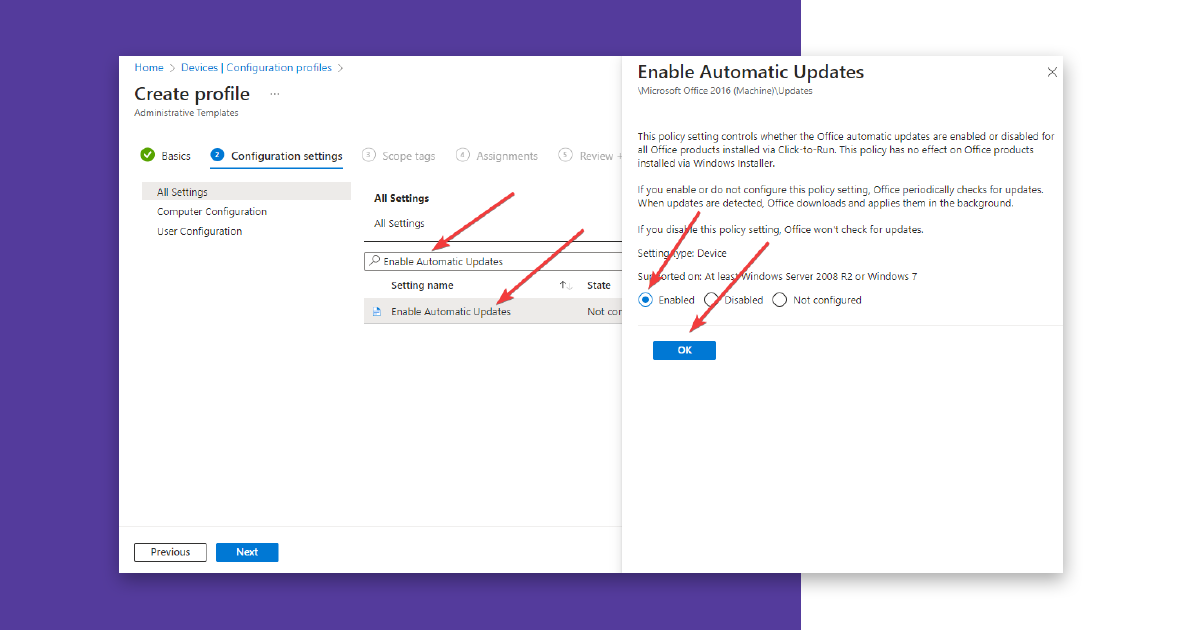
Now enter “Enable Automatic Updates,” click on the entry again, and activate this setting. Please confirm with “OK” and now click on “Next”.
Scope tags are not required, so you can skip this tab with “Next.”
As an assignment, you must now select a group that includes all your Windows devices to be updated.
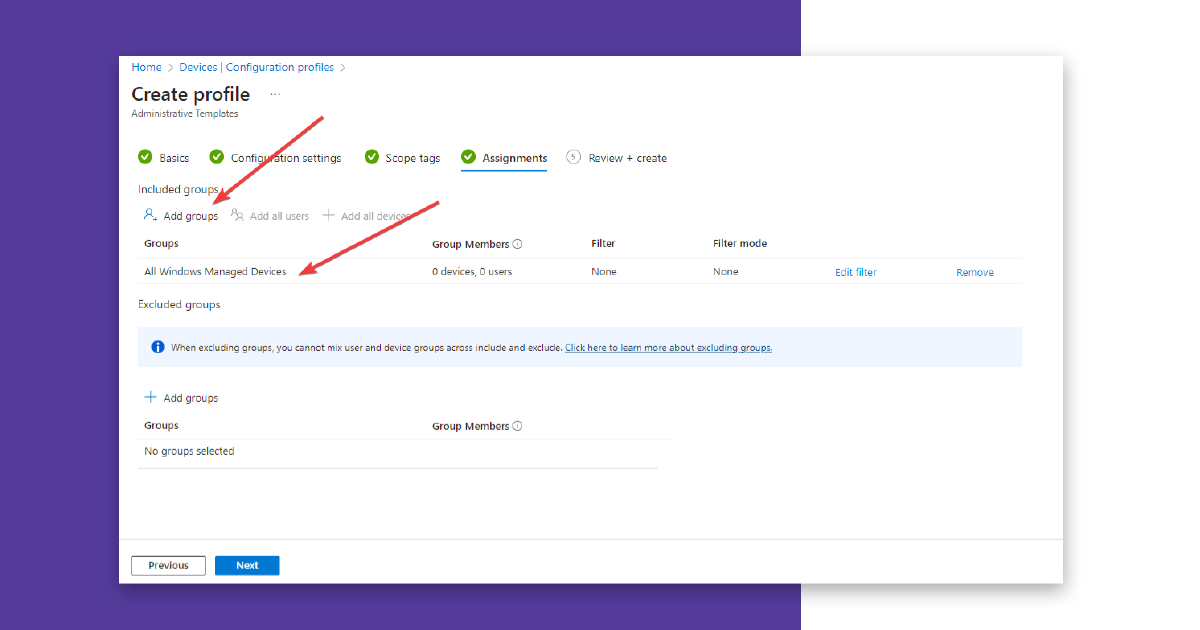
Click on “Next” one last time, and a summary will be shown.
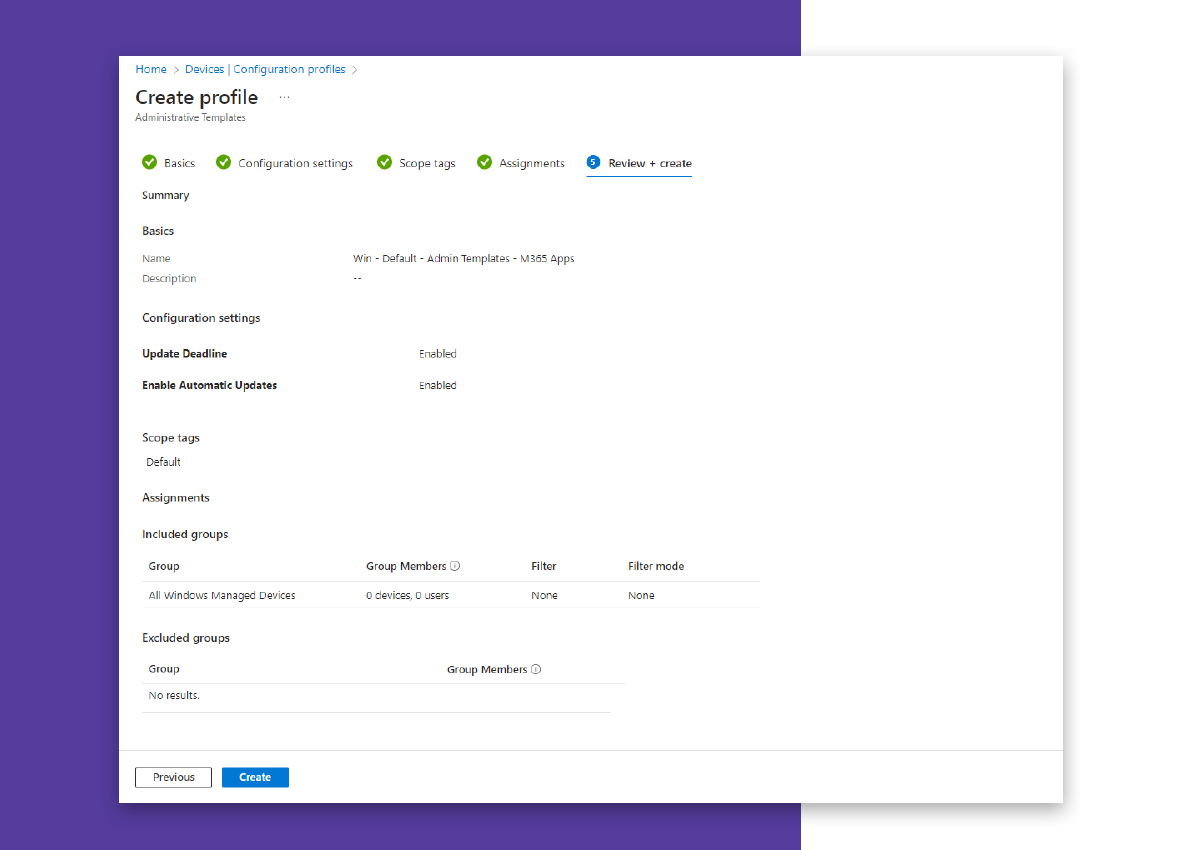 With “Create,” the Intune Administrative Template is created and applied to the group’s computers.
With “Create,” the Intune Administrative Template is created and applied to the group’s computers.
If your company is unable to roll out these security updates immediately, or if you want to take additional measures until a successful rollout, it is recommended to block outgoing network traffic to Internet IP addresses for the SMB protocol (TCP 445) with a firewall or through VPN settings. This prevents information from flowing to the attacker. This can also be done on the endpoint itself using the Microsoft Defender Firewall.
To check if your environment was the target of this attack, it is recommended to run Microsoft’s script on Exchange Online or Exchange on-premises. It checks all mailboxes for suspicious messages.
If you are using Microsoft Defender for Endpoint, you can use the following Advanced Hunting Query to detect corresponding network connections in your environment:
| where Timestamp > ago(30d)
| where RemoteIPType == "Public" and RemotePort == "445"
| where InitiatingProcessVersionInfoOriginalFileName =~ "outlook.exe"
or InitiatingProcessParentFileName =~ "outlook.exe"